| Attention Before you read this post, I highly recommend you check out my resources page for access to the tools and services I use to not only maintain my system but also fix all my computer errors, by clicking here! |
When it comes to hacking, there are so many different programs an individual can use to decrypt or guess a password for a variety of account types and applications. If you already know a thing or two about how to hack passwords, then as a potential victim, you can take the necessary steps to protect your passwords form being stolen. The various password hacking programs use a variety of algorithms for the various password systems out there. This means an individual with enough experience can determine what he/she needs for a specific job.
The types of hacking methodologies adopted by these password hacking tools are as follows:
- Dictionary Attacks
- Brute Force Attacks
- Known Ciphertext attacks
Each individual password hacking tool tends to be designed specifically for a type of password protection system. An example of this would be hacking tools for Zip passwords, Microsoft Office passwords, and Network Router passwords.
When it comes to learning how to hack passwords, if you were to use a password cracking calculator in order to determine the length of time it will take to decrypt a password with a specific password hacking tool, you will find that it can take anywhere from 5 minutes to several months, depending on how complex the password protection system is.
How to Hack Passwords Using Dictionary Attacks
The dictionary attack algorithm works by exploiting the fact that a great many people have a tendency to use simple words for passwords. A dictionary attack involves a password hacking tool using every word in the dictionary as a possible password. When learning how to hack passwords you will find a great many of such tools that attempted to hack or rather guess a password using the dictionary attack algorithm.
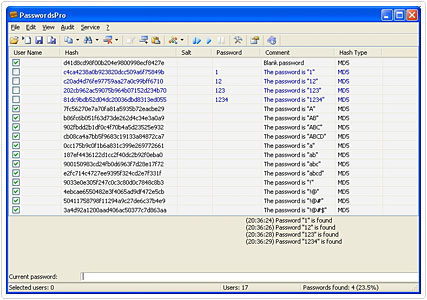
There are also the more advanced dictionary attack based tools that will use a combination of both words and variations. One particular password variation that is fairly common is the replacement of the letter ‘I’ with the number ‘1’ or the letter ‘E’ with the number ‘3’. Another password combination strategy is the utilisation of two small words with a number in the middles, such as “boys2men” or “love4you”.
Brute Force Attacks
If your first attempt is with a dictionary based hacking tool and that fails, then a brute force attack should be the next option on the table, when looking at how to hack passwords for the very first time. A brute force attack is basically when every possible password is attempted. As a result, brute force attacks can that an inordinate amount of time circling through all the different password variations. The general consensus on time is that, the longer the password length (in terms of letters and/or numbers), the more time you will have to wait for it to discover the password.
Known Ciphertext Attacks
The known Ciphertext attack method utilises cryptanalysis in order to determine the plaintext password from its Ciphertext counterpart. If the encryption algorithm for the password system doesn’t have any known weaknesses, then the password hacking tools will use either a brute force or a dictionary attack in order to try and guess what the password is.
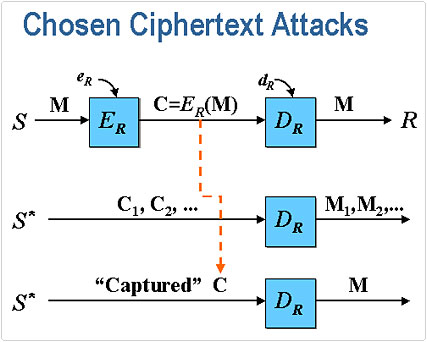
When you have a cryptosystem that has been exposed to known ciphertext attacks, the implementer must adopt a strategy where they stay clear of the particular conditions which could lead to an enemy decrypting said ciphertexts. This can be a fairly complex task, as even the more unknown ciphertexts are vulnerable to attack. Just like the other attack methodologies, known ciphertext attacks can be non-adaptive or adaptive.
With the non-adaptive attack, the hacker begins by selecting a ciphertext to decrypt. The hacker initiates the attack, without using the plaintexts which would otherwise be used to notify their preference for ciphertexts. With the adaptive approach, the hacker will make their preferences adaptively by basing it on what the outcome is for the former decryptions.
Prevention
The most effective and efficient method of preventing hackers from obtaining a system password is to prohibit him/her from gaining access to the hashed password. For example, on Unix based systems, these hashed passwords can be found stored in the /etc/passwd file. On other versions of Unix systems, you can find the passwords stored in the /etc/shadow file, with access restricted only to those with the correct privileges. This prevents hackers from gaining access to the file, for obvious reasons. However, despite this fact, vulnerabilities still exist in many network protocols, as they still transmit their passwords using cleartext or some other not so secure method.
Creating Passwords
Once you learn how to hack passwords, it then puts you in the better position to stop them. A password that is easy for you to remember is usually easy for a hacker to guess. Passwords that are a lot more difficult for an individual to remember, actually decrease the security level of a system, this is because:
- Users may be required to write the password down on paper or save it in a file on their system.
- Users will likely have to reset their password on a frequent basis.
- Such users are more likely to use the same password universally.
With that said, users can increase the strength of their password, without having to create a difficult-to-remember password by mixing lowercase and uppercase letters and numbers, or by changing their password on a monthly basis.
From various studies conducted on the security and memorability of passwords, it has been found that passwords that are based on a particular phrase, that have been strengthened by substituting certain letters for numbers, are just as easy to remember, as a more naively chosen password, and are just as difficult for a hacker to obtain. Another good method involves combining two unrelated words together; having an algorithm that generates obscure passwords on a constant basis, is another good secure method.
More and more people are becoming aware of the various methods that they can use to make their passwords less difficult to guess for those who know how to hack passwords. However, if you were to ask an individual to remember a password that consists of both uppercase and lowercase letters, they would find it just as difficult as remembering a sequence of numbers. On the flip side, asking an individual to create a password using letters and numbers, usually results in them creating easy-to-guess substitutes, such as ‘a’ -> ‘@’ and ‘E’ -> ‘3’, these substitutes are well known to hackers, so it’s important that users be a little more creative when mixing numbers and letters.
Here are a number of useful tips that one should think about when creating a password:
- Randomly substitute numbers for letters, but don’t make it too obvious; substituting the letter ‘S’ for ‘6’ for example.
- Use capital letters every now and then, but have some structure to it, so that you can more easily remember it.
- Never use someone’s name for your password, as it will fall under a brute force attack.
- Think of something a little more obscure for your password.
- Try to create new password and usernames for everything. This way, if a hacker manages to figure out the password to your email account, he/she doesn’t automatically gain access to every other service you have a password for.
- Because it’s likely you’ll have difficulties remembering all your different passwords, using a Windows based password tool is a good option, as the passwords will be kept in encrypted form. It will also automatically fill in the username and password, whenever you visit a login page. You can also find specific tools that allow you to export all your passwords to your Smartphone, PDA or USB memory stick.
- For Mac users, 1Password is an excellent tool. It works similarly to Roboform, in that it can be used to save all your passwords for all the different websites and services you access on your system.
- Microsoft has its own password strength tester that I recommend you use whenever you think of a password.
Hacking Software
When learning how to hack passwords there are tons of different password hacking tools out there, but the most popular ones are as follow:
- Cain and Abel
- John the Ripper
- Hashcat
- Hydra
- DaveGrohl
- ElcomSoft
Many software packages also come with password hacking features. The vast majority of these packages utilise both dictionary and brute force attack algorithms, as they’ve proven to be most effective.
Are you looking for a way to repair all the errors on your computer?

If the answer is Yes, then I highly recommend you check out Advanced System Repair Pro.
Which is the leading registry cleaner program online that is able to cure your system from a number of different ailments such as Windows Installer Errors, Runtime Errors, Malicious Software, Spyware, System Freezing, Active Malware, Blue Screen of Death Errors, Rundll Errors, Slow Erratic Computer Performance, ActiveX Errors and much more. Click here to check it out NOW!


Heya i am for the first time here. I came across this board and I find It
truly useful & it helped me out much. I am hoping to present one thing again and aid others such as you aided me.
whoah this weblog is wonderful i love studying your posts.
Keep up the good work! You already know, lots of individuals are searching around for this info, you can aid them greatly.