| Attention Before you read this post, I highly recommend you check out my resources page for access to the tools and services I use to not only maintain my system but also fix all my computer errors, by clicking here! |
The removal of a Trojan horse virus is likely of utmost importance to you; however, before we get to it, let me first elaborate on exactly what a Trojan horse is.
A Trojan horse virus is basically a small program that is designed to either hijack or disrupt applications within your computer system. These viruses tend to work as an intermediary for other types of viruses such as spyware. The Trojan horse breaks down your computers security protocol in order to render it vulnerable to threats from other kinds of infections.
The automated approach, which entails the use of anti-spyware software, is usually sufficient in removing this kind of threat. So it should be the first step that you take before you attempt more advanced procedures.
The DIY Approach to Your Trojan horse virus
Unfortunately, there are times when the automated approach does not work despite all efforts. In such situations, all is not lost, as it is possible for you to manually identify the offending file(s) and remove them from your systems directory and registry.
The type of effect the Trojan horse virus may have on your machine varies somewhat, from altering the settings of your keyboard/mouse to corrupting your master boot record. Your ability or inability to reverse the adverse changes to your system will depend a great deal on your knowledge of computers; however, thanks to the internet it is possible for you to find places online (such as this website) where you can find step by step instructions on how to properly remove a Trojan horse.
Identifying the Virus
If you already know what virus your computer is infected with, then you can skip this section. Before you can ever hope to remove the infection, you must first identify the virus on your computer. The good thing is that you should already have some kind of indication of the type of Trojan horse you have in your computer.
In most cases, when a system is infected with a Trojan horse, it will display repeated error messages stating that an abnormality is occurring in a program. These messages are called DLL errors. The specific DLL process will be directly linked to the Trojan horse, which means, if you are able to identify the defective DLL file, then you will be able to determine the virus.
There are many different websites that you can go to, for the identification for specific DLL files. Just keep a log of the error message and type it into the search box of http://www.processlibrary.com for the appropriate information. If your computer is indeed infected with a Trojan horse, then it will give you the executable (EXE) file name for it.
Display System Files
If your system files are set to hidden, then it will make it very difficult for you to remove the Trojan horse virus from your computer, this is because it is likely that you will have to search through sensitive system files in order to find the virus. Simply follow the instructions below to display all hidden system files.
1. First, ensure you’ve logged into your computer with administrative rights.
2. Once your computer has finished booting up, click on Start -> My Computer. [Windows Vista/7: Computer]
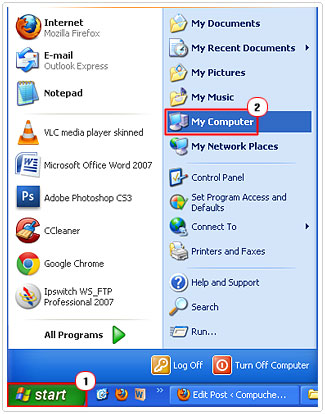
3. When My Computer loads up, click on Tools -> Folder Options. [Windows Vista/7: Organize -> Folder and search options]
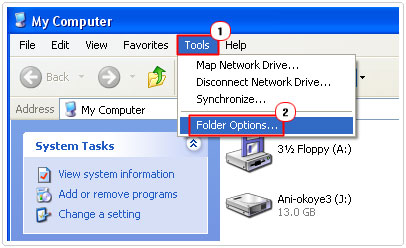
4. From Folder Options, click on the View Tab and scroll down and uncheck the boxes next to Hide extensions for known file types and Hide protected operating system files. Then click on Apply and OK.
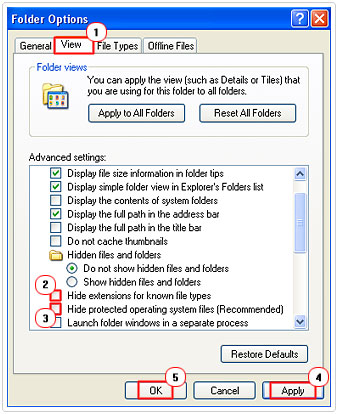
Note: You will be presented with a warning message when you attempt to unhide your operating system files, be sure to click on Yes to bypass it.
Disable System Restore
If system restore is on during the repair process, then it will keep a shadow copy of all the files that you have deleted and/or modified, that includes files that have been infected with the Trojan horse virus. As a result, it’s very important that you disable system restore before you start making any real changes to your operating system state.
In order to disable this feature simply follow the instructions on my post on System Restore.
Scan Your System in Safe Mode
It’s best that you run a full system scan using anti-malware software, before you attempt any manual methods of removing the threat. In addition, there is also the issue of certain infected files on your system being locked, which will prohibit any software from removing these particular files in a normal Windows environment. As a result, you’ll want to boot into safe mode (which is the diagnostic mode of the OS), as it will increase the chances of the software being able to detect and remove the Trojan horse virus.
Booting into Safe Mode is fairly easy. Simply restart your system and press the F8 key after the POST (Power on Self Test).
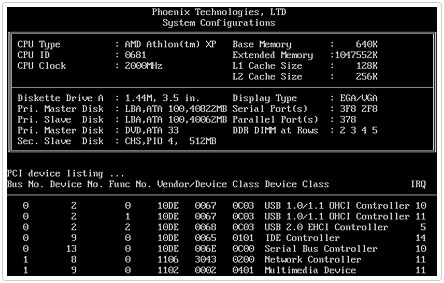
Then select Safe Mode from the Advanced Boot Option Menu and hit Enter.
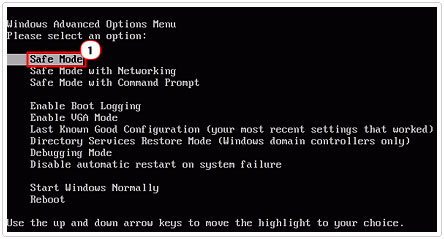
There are a number of anti-spyware/malware applications out there that you can use to remove the virus from your system. But I personally recommend you use SpyHunter, which is amongst the very best and is most likely to remove the virus without ever having to dabble in any manual techniques.
You can get a hold of this program here:
CLICK HERE TO CHECK OUT SPYHUNTER
Additional Notes
Before you make any attempts to remove the Trojan horse, you’re going to want to close any additional processes that you feel may be related to the Trojan horse.
1. Once in Safe Mode, press CTRL+ALT+DEL to load up Windows Task Manager. Once Windows Task Manager loads up, click on the Processes Tab.
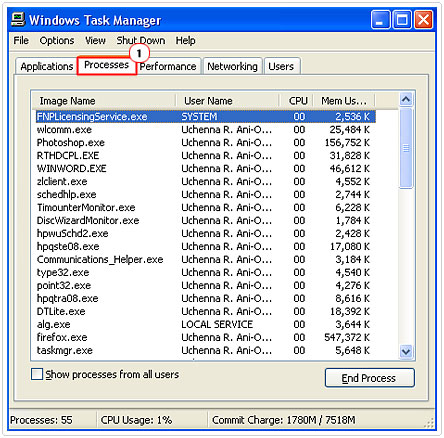
2. From here, you’ll to want to highlight nonessential third-party processes and click on End Process, followed by Yes to the warning message.
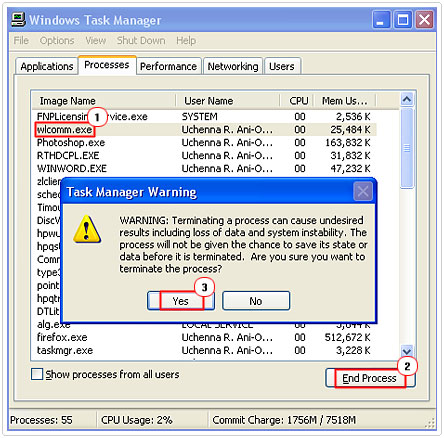
Editing the Registry
Before you can be sure the Trojan horse has been completely removed from your system, you’ll first need to ensure there are no traces of it in your registry. This will prevent it from replicating itself. Because the Trojan horse is an executable file, that means you should be able to find it in the RUN folder of your systems registry.
Carrying out the steps below will ensure the Trojan horse virus doesn’t replicate itself when you reboot into a normal Windows environment.
WARNING: Deleting or editing the wrong registry entries can irreparably damage your operating system.
1. First, be sure to remain in Safe Mode with the appropriate administrative rights.
2. Then click on Start -> Run [Windows Vista/7: Press  + R], type in regedit and click on OK.
+ R], type in regedit and click on OK.
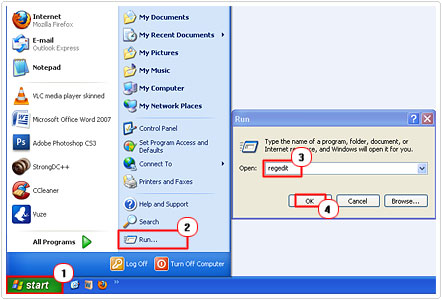

3. Once Registry Editor loads up, navigate to the following path:
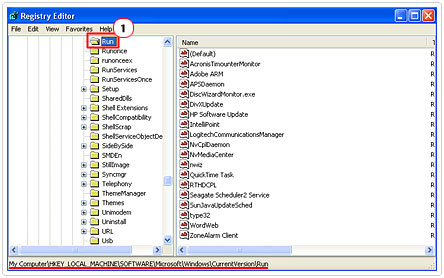

4. In the section to the right, highlight and Delete all the Executables and DLLs that are associated with the Trojan horse in question.
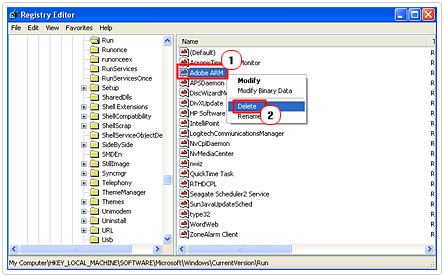

Check Your Startup Programs
The last thing you’ll want to do is remove all files and programs associated with the Trojan horse virus that load up during the boot phase. You can do this by following the instructions below.
1. First, ensure your still in Safe Mode with administrative rights.
2. Then click on Start -> Run [Windows Vista/7: Press 


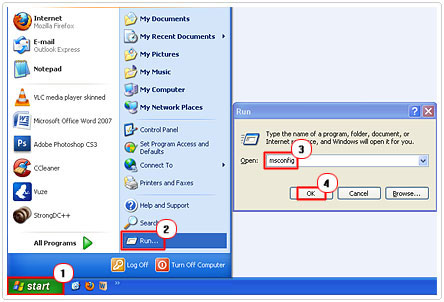

3. Once System Configuration Utility loads up, click on the Startup Tab. From the Startup Tab, uncheck all Startup Item(s) that are associated with the Trojan horse. Then click on Apply -> Close and restart your computer.
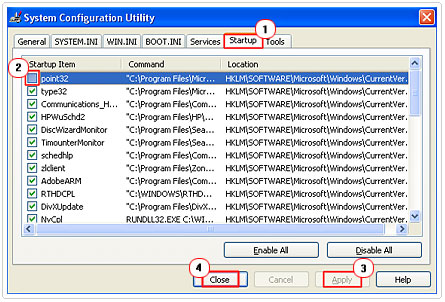

You should only attempt to remove the Trojan horse manually, if the automated method doesn’t work. However, installing and running SpyHunter is usually sufficient in rectifying problems such as this.
Are you looking for a way to repair all the errors on your computer?


If the answer is Yes, then I highly recommend you check out Advanced System Repair Pro.
Which is the leading registry cleaner program online that is able to cure your system from a number of different ailments such as Windows Installer Errors, Runtime Errors, Malicious Software, Spyware, System Freezing, Active Malware, Blue Screen of Death Errors, Rundll Errors, Slow Erratic Computer Performance, ActiveX Errors and much more. Click here to check it out NOW!


Yes, you are right it’s generate the bsod error after attack. I have faced the same problem, when the VirTool:Win32/Obfuscator.XX virus attack on my system, then my computer process becomes poor. Actually it is a trojan worm, that is specially created to damage the user’s data. I have removed this virus permanently from my desktop by applying some easy steps.
I do acknowledge as valid with every one of the thoughts you have presented for your post. They are truly persuading and will work. In any case, the posts are exceptionally concise for beginners. May just you please stretch them a bit from ensuing time? A debt of gratitude is in order for the post.