| Attention Before you read this post, I highly recommend you check out my resources page for access to the tools and services I use to not only maintain my system but also fix all my computer errors, by clicking here! |
The question of what is spam can be summed up as the nefarious use of electronic messaging services and systems to send unsolicited messages to unexpected mail users. These messages are usually advertisements for a particular service or product. While email spam is the most recognised form of spam, there are a number of other similar abuses that fit into this category, such as: messaging spam, mobile phone spam, social networking spam and spam in blogs.
Spamming is a very lucrative, though unscrupulous way of making money, as operating costs are nonexistent, outside of managing the various mailing lists, and it’s also very difficult for the sender to be held accountable for his/her actions, giving the spammer a sense of security. Because the level of difficulty in spamming is relatively low, this makes it most appealing, resulting in an ever increasing number of unsolicited emails. There were seven trillion unsolicited emails in the year 2011 alone. All of this amounts to increasing costs, due to lost productivity and fraud, leaving the internet service providers and end user to fork the bill.
Email Spam
So what is spam, the email kind; being bombarded with various unsolicited emails such as fake bank emails, adult services emails, payday loan emails and various pharmaceutical products emails, is something that we’ve all become accustomed to nowadays. However, through the use of a spam filter, it’s possible for you to thwart these emails, providing you take the appropriate steps.
Over 90% of all emails sent over the internet are spam; this means email users spend a considerable amount of time, deleting most of the mail they receive. The unfortunate development is that spammers are becoming increasingly more sophisticated, producing more authentic looking emails, that many people are now falling victim to.
Spammers usually purchase very large email lists from third party businesses. You could fall prey to a spammer if you:
- Post messages on a forum
- Give your email address to online business
- Sign up to any service
- Market your email address on your personal website.
Stopping Email Spam
Your approach to tackling spam is what is most crucial.
- Never click on the links inside emails that have been sent by someone you are unfamiliar sender.
- Never purchase anything from an unsolicited email. As you run the risk of not only compromising the security of your system, but also infecting it with a virus.
- Never reply to spam emails.
- Never threaten a spammer. This is because the spammer has rights too, so using threatening language in your response to him/her could land you in trouble.
- Consider using multiple email address. You could setup an email account specifically for buying things online, and if it starts to become cluttered with junk emails, then you can simply discard it and start another.
- Make sure you never reveal your email address on any websites you frequent. This is will prevent spam bots from harvesting it.
Spam Filters
Spam filters are ingenious tools that are capable of blocking a good amount of unsolicited emails, the idea is that laypersons will never have to know what is spam with the implementation of this tool. Many email services today, come with spam filters as standard. One thing you should be aware of is a feature called white-listing, as its implementation means, you will have to actively mark certain emails as Not Spam otherwise they can get caught up in the Spam folder.
It’s not uncommon for people to miss certain emails due to this feature, despite the fact that the email is still retrievable, in the Spam folder. Thus, it’s very important that you mark known email address as Not Spam.
Instant Messaging Spam
Instant messaging spam or Spim, as it’s also called, is when spam messages are sent through instant messaging (IM) services. Although not quite as expansive as email spam, it continues to grow, reaching more users each year. 10 years ago, there were reports of over 500 million spam messages being sent over IM services, a number that doubled the following year. As it becomes more and more commonplace, it will start to have a negative impact on the business world, as it will begin to eat away at cooperate resources, creating all new security problems.
When tolling the line of what is spam, IM is one of the most convenient avenues for spammers nowadays. This is primarily due to the fact that IM users are more likely to click on the links in the messages they receive. Another luxury these spammers enjoy is being able to bypass any firewall or antivirus software, when attempting to get malicious software onto the host’s computer. The good news is that corporations, governments and ISPs are all working together to combat spam of this form; the implementation of the Can-Spam Act of 2003 is just one of the many measures taken to combat this problem. As more and more anti-spam measures are put in place, essentially frustrating your conventional spammer, these individuals will slowly move into instant messaging spam.
One of the most effective ways for you to protect yourself from Spim is to block messages from people, who are not on your buddy list, or to create a permission list and only allow messages from those you put on it. To do this, in the 3 most popular IM programs, follow the instructions below:
Yahoo! Messenger
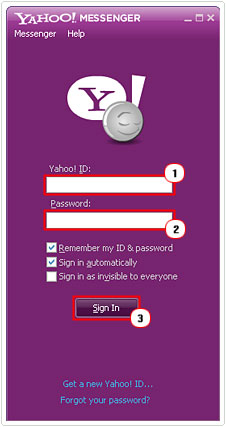
1. Load up Yahoo! Messenger, and then log in by putting in your Yahoo! ID and Password and clicking on Sign in.
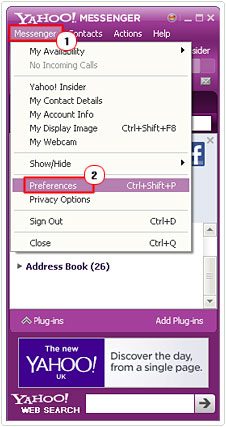
2. Once logged in, click on Messenger -> Preferences.
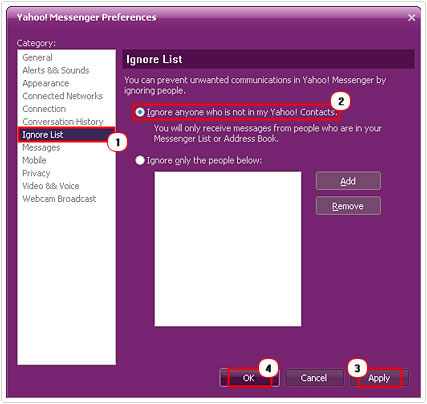
3. This will bring up the Yahoo! Messenger Preferences applet, from here click on Ignore List on the left hand column. Then select Ignore anyone who is not in my Yahoo! contacts, then click on Apply and OK.
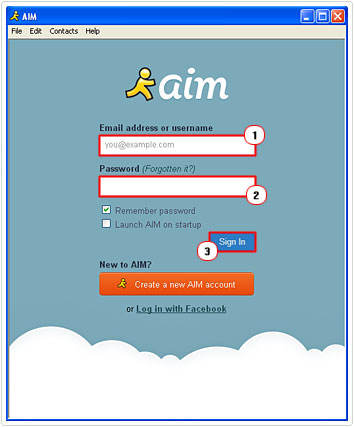
AOL Instant Messenger
1. Load up AIM, then put in your Email address or username and Password and click on Sign in.
2. Once it’s loaded up, click on File -> Preferences.
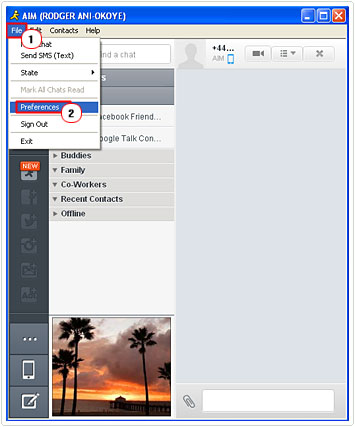
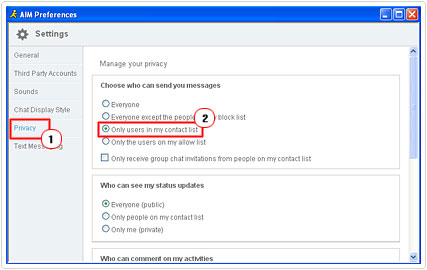
3. This will bring up AIM Preferences, from here click on the Privacy Tab, and then click on Only users in my contact list, then close the applet.
Skype
1. First, load up Skype and then click on Skype Name (if you have a Skype Account) or Microsoft Account (if you’re migrating from MSN Messenger).

2. Then put in your Account Name/Email and Password, and click on Sign In.
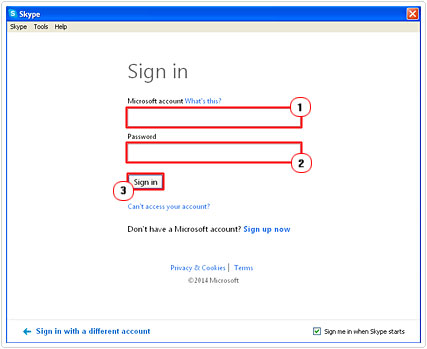
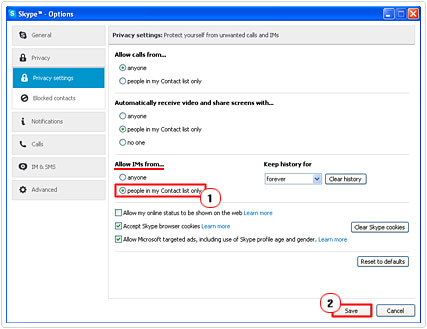
3. Once Skype has logged in, click on Skype -> Privacy.
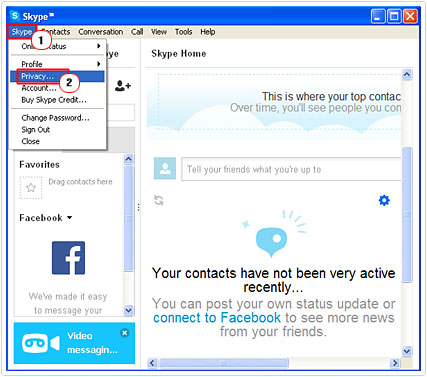
4. This will bring up Skype Options, from here click on people in my Contact list only, under Allow IMs from… and click on Save.
Mobile Phone Spam
So what is spam in this form; mobile phone spam, though not exclusively, is directed primarily at the text messaging component of mobile phones, and it goes by a number of different names such as text spam, mobile spamming, m-spam and SMS spam.
During the rapid rise in popularity of mobile phones, which was around the early part of the 2000s, frequent users of the text messaging service began to notice an increasing number of unsolicited messages being sent to their mobile phones, much of which were advertisements for products and services, such as payday loans and life insurance policies. The most annoying part about mobile phone spam is that, unlike with email spam, it is possible for the recipient to be charged for every message that they receive, and that includes what is spam.
Mobile phone spam isn’t nearly as widespread as email spam, where email users can expect over 90% of the email they receive to be spam. The amount of mobile phone spam that a phone user may receive varies, depending on where he or she lives. In North America for example, mobile phone spam has experienced upward growth for the past couple years, however despite this revelation, it still only stands at 1% of all text messages sent over a phone. In parts of Asia on the other hand, you can expect over 30% of all text messages you receive on your phone to be what is spam.
The stark difference between the actions of the mobile phone spammers across the world can be attributed to the differences in costs (to the spammer) and any technological barriers, such as law enforcement agencies, that exist in certain parts of the world. Today, you will find that the vast majority of mobile phone spam is sent using a prepaid unlimited messaging rate plan.
Blocking Mobile Phone Spam
There are a number of things you can do to curtail what is spam on your phone. However, some of the more successful methods are as follows:
- Block all text messages to your phone that have been sent from the internet. Because the vast majority of mobile phone spam is sent from the internet, asking your phone provider to block all internet messages from reaching your phone is a good place for you to start.
- Consider creating an alias. If you would still like to receive certain internet messages, such as those sent by a company that you frequently patronise, then you could create a unique alias, that way all messages addressed specifically to that alias will get through, whereas everything else will be blocked. This acts as a filter, blocking the spammers, who typically find their mark, by sending text messages to random numbers. Just be sure to only give your alias out to websites and people that you would like to receive internet messages from.
- If you have a phone provider that allows you to block all text messages except those that have been sent to a specific address, then you could open up an email account that has built in anti-spam software then have all your text messages funnelled through that email account, by giving out that specific email address to others.
- Block a specific website, phone number of email address. The vast majority of phone providers provide this feature as standard, and it can come in handy, especially if you’re dealing with a persistent spammer.
What Is Spam in Blogs
Blog spam, comment spam or social spam as it’s sometimes called, is a form of spamdexing (a technique used for manipulating the search engines). These spammers typically use automated tools to post random comments, copy information from other websites, or promote a product to a specific wiki, blog or guestbook. Any web resource that accepts links that are submitted by visitors is targeted by these spammers.
Why Comment Spam Is So Bad
There are many site owners out there, that feel, (in an attempt to inflate the number of people commenting on their posts, unaware of what is spam) that it’s a good idea to approve, virtually every comment under their posts, even those that are not relevant to the topic discussed in the posts. Well this behaviour is harmful, for a number of reasons, because:
- Google has recently started to come down heavily on bad links. This recent behaviour by Google, not only encompasses sites that purchase links, but also those that perpetuate it. Thus, it’s in your best interest to ensure that you are not allowing bad links on your site, as its effects can be longstanding.
- A site that has a lot of comment spam on it shows to others that it is not being properly moderated. A site that lacks proper moderation, paints an ugly perception of itself in the eyes of its visitors.
- There’s also that possibility that you could lose readers to your site. Being aware of where all the links in your site are pointing to is important, because an unsuspecting reader could click on one of these links and be taken to a totally irrelevant website.
Anti-Spam Plug-ins
There is a number of plug-ins out there that are designed specifically for reducing the amount of comment spam to your blog, eliminating the need to ever know what is spam. The more popular ones are as follows:
- Akismet – This plug-in comes with your WordPress blog, and acts as a filter, filtering out all the comments that it feels is spam. In order for you to activate it, you will need an API key, which you can acquire from the Akismet website. For personal blogs, it’s free to use, but for non-personal blogs, you can expect to pay up to $50 per month. This tool is not completely foolproof, which means, you will need to check your spam folder from time to time, as you may find some legitimate comments in there.
- CommentLuv – This is another spam-related plug-in. This tool allows the author to leave a link to the latest post on their website, every time they leave a comment on your site. This tool has the added advantage of encourage commenting, while at the same time, filtering out spammers.
Note: Click on the plug-ins name for more information, your recommended solution, knowing what is spam is only the first step to combating it.
Social Networking Spam
This kind of spam is directed at those who use one of the many social network services such as Facebook, LinkedIn, Google+, Pinterest and MySpace. Estimates put the amount of social media spam accounts at 40%, this is because many such social media users know little of what is spam, to effectively combat it. Through these accounts, spammers can do a demographic search or browse the various groups and fan pages in order to send their notes. These notes will usually contain links to various products and services. In an attempt to combat this trend, many social networks have implemented a ‘report spam/abuse’ button or an address which you can forward such notes to. However, spammers have their own countermeasures in place, which involve moving from one fraudulent account to another.
The Various Types of Attacks
For those who want to know what is spam, users have a number of different avenues available to them when it comes to creating content on social network sites. However, spammers are also privy to these tools, which they use to their own end. The types of attacks one might encounter are as follows:
Like-jacking attacks: The concept behind this particular attack is fairly simple. These cybercriminals begin by creating an interesting post, which is used as bait. To ensure its popularity, these criminals will typical create a post around celebrity news, hot gossip or social events.
Users, who then click on the links, unintentionally act as accomplices, as the malicious script within the post, reposts, all the videos, links and/or images to the wall of the user. A more modified version of this particular attack entails getting the user to ‘like’ a post without their consent, in order to perpetuate itself around the website.
Spam Tweets: Cybercriminals utilise Twitter’s character limitation to their own end, by creating multiple short but interesting tweets that have links in them. This is were knowing what is spam, comes most in handy, an example of these tweets may include a promotion for free vouchers, a brief testimonial for a service or product or an advertisement for a job. There are also Twitter spam tools, which makes the whole process that much easier.
Malware Downloads: In addition to spam tweets, cybercriminals also use twitter to spread tweets that have links to pages that contain malware on them. A more sophisticated version of this method involves using video-related posts, which leads to a fake YouTube page where the intended purpose is that the unsuspecting user will download a malicious file to their computer.
How Can You Prevent These Attacks?
The type of anti-spam measures you’d adopt for email and web spam is still applicable here for avoiding most threats in the social media theatre. Users need to train themselves to be cautious of fraudulent notifications which are styled to appear legitimate. When browsing the pages and profiles of users, it also important that users know what is spam, so they will understand that they are vulnerable to malicious scripts and files. Despite the sense of community that exists within these social networks, users shouldn’t forget that cybercriminals are on the prowl, looking for any little opportunity to exploit.
Users should also make a consorted effect to protect their data. Users should see things from the perspective that all things that are posted online, are accessible to the general public. Apart from being cautious when posting, users should also never share any sensitive information through private chat sessions or messages. As this information can easily be extracted if your account is hacked.
To prevent this from happening to oneself, it’s very important that you familiarise yourself with the security settings of the social media site that you use. For example, on Facebook it’s possible for you to create access lists, which you can use to control the kind of information that people can see. In addition, enabling secure connection options (HTTPS) on both Twitter and Facebook adds an additional layer of protection, as it will encrypt all data.
Are you looking for a way to repair all the errors on your computer?

If the answer is Yes, then I highly recommend you check out Advanced System Repair Pro.
Which is the leading registry cleaner program online that is able to cure your system from a number of different ailments such as Windows Installer Errors, Runtime Errors, Malicious Software, Spyware, System Freezing, Active Malware, Blue Screen of Death Errors, Rundll Errors, Slow Erratic Computer Performance, ActiveX Errors and much more. Click here to check it out NOW!


I am really impressed together with your writing abilities as smartpy ass with the
structure foor your blog. Is that this a paid topic or did you modify it your self?
Anyway keep up the nice quality writing, it is rare to look a
nice weblog like this onne today..
Nice Info which you have provided here. I like this types interesting topic. Keep it up
Praveen
Nice Info which you have provided here. I like this types interesting topic. Keep it up
Praveen
I’m not that much of a internet reader to be honest but your
sites really nice, keep it up! I’ll go ahead and bookmark your website to come
back down the road. All the best
Helpful info. Fortunate me I discovered your site by
chance, and I am shocked this twist of fate didn’t took place in advance!
I bookmarked it.
That is a good tip particularly to those new to the blogosphere.
Simple but very accurate information… Appreciate your sharing
this one. A must read post!
It’s really a nice and useful piece of info. I am happy that
you shared this useful information with us. Please keep us informed.
Thank you for sharing.
This site was… how do you say it? Relevant!!
Finally I have found something that helped me.
Cheers!
Good post! We will be linking to this particularly great post on our website.
Keep up the great writing.
You ought to be a part of a contest for one of the most
useful blogs on the net. I most certainly will recommend this site!
Nice post. I learn something new and challenging on blogs I stumbleupon on a
daily basis. It will always be interesting to read articles
from other writers and use a little something from other web
sites.
There’s definately a lot to learn about this subject.
I love all of the points you’ve made.
Your style is really unique in comparison to other people I
have read stuff from. Many thanks for posting when you’ve got the opportunity, Guess I’ll just book mark this blog.
Good day! I just would like to give you a huge thumbs up for the excellent info you have got right
here on this post. I am coming back to your website
for more soon.
Good blog! I really love how it is simple on my eyes
and the data are well written. I am wondering how I could be notified whenever a new post has been made.
I have subscribed to your RSS which must do the
trick! Have a great day!
I think this is one of the most important info for me.
And i’m glad reading your article. But wanna remark on few general things, The website
style is perfect, the articles is really great : D.
Good job, cheers
Magnificent web site. Lots of helpful info here. I am sending it to a few pals ans additionally sharing in delicious.
And of course, thank you on your effort!